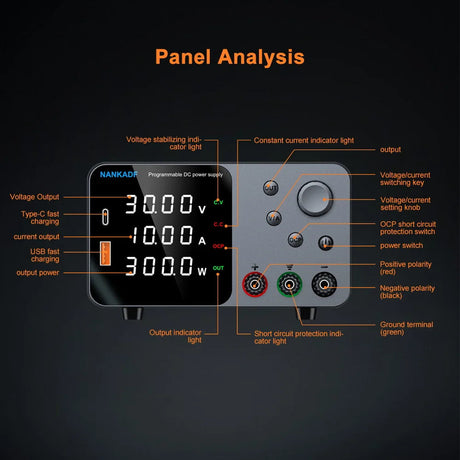
JTAG (Joint Test Action Group) is a widely used protocol for debugging, programming, and testing integrated circuits (ICs). It allows direct communication with a chip to read its memory, perform boundary scans, or load firmware. This tutorial will guide you through the basics of using JTAG to read chips, including setup, tools, and best practices.
What is JTAG?
JTAG is a standardized interface (IEEE 1149.1) that provides a way to test and debug hardware at the chip level. It is commonly used in:
- Firmware development and debugging
- Testing PCB connections
- Flashing firmware onto devices
- Extracting memory from ICs
JTAG uses a 4 or 5-pin interface:
| Pin | Description |
|---|---|
| TDI | Test Data In |
| TDO | Test Data Out |
| TCK | Test Clock |
| TMS | Test Mode Select |
| TRST | Test Reset (optional) |
What You Will Need
- JTAG Adapter: A hardware device to interface with the chip (e.g., SEGGER J-Link, OpenOCD-supported adapters).
- Target Device: The IC or system you want to read.
- Software Tools: Applications for JTAG debugging, such as OpenOCD, urJTAG, or proprietary tools.
- JTAG Pinout Documentation: Pinout diagram for the target device.
- Connection Accessories: Wires, headers, and a breadboard (if necessary).
Step 1: Setting Up the JTAG Hardware
1. Identify the JTAG Interface on the Target Device
- Refer to the chip’s datasheet or PCB schematics to locate the JTAG pins.
- Common labels for JTAG pins include
TDI,TDO,TCK, andTMS. - Some boards have labeled JTAG headers (e.g., 10-pin or 20-pin connectors).
2. Connect the JTAG Adapter
- Wire the adapter to the target device, matching the JTAG pinout:
-
TDIon the adapter connects toTDIon the device, and so on. - Ensure GND is connected between the adapter and the target.
- Provide power to the target device if necessary.
-
3. Verify Voltage Levels
- Ensure the JTAG adapter supports the voltage levels of the target device (e.g., 3.3V or 1.8V).
- Some adapters have configurable voltage settings.
Step 2: Installing JTAG Software Tools
1. OpenOCD (Open On-Chip Debugger)
OpenOCD is an open-source tool widely used for JTAG debugging.
- Install it using your package manager (e.g.,
apt install openocdon Linux). - Ensure your JTAG adapter is supported by OpenOCD.
2. urJTAG
A lightweight tool for boundary scan and basic JTAG operations.
- Install via urJTAG’s website.
3. Vendor-Specific Tools
For proprietary adapters like SEGGER J-Link or Xilinx, use their official software:
- SEGGER J-Link: Download the J-Link tools from SEGGER’s website.
- Xilinx Tools: Use Vivado or iMPACT for FPGA debugging.
Step 3: Reading Data from a Chip
1. Configure the JTAG Software
- Create or load a configuration file specifying the JTAG adapter and target device.
- Example for OpenOCD:
source [find interface/jlink.cfg] transport select jtag source [find target/stm32f4x.cfg] init halt
- Example for OpenOCD:
2. Detect the Target Device
Run a command to scan the JTAG chain and identify connected devices.
- For OpenOCD:
Look for detected devices in the output log.openocd -f interface/jlink.cfg -f target/stm32f4x.cfg
3. Dump Memory Contents
Use JTAG commands to read memory regions:
- For OpenOCD:
dump_image memory.bin 0x08000000 0x10000-
memory.bin: File to save the memory dump. -
0x08000000: Start address. -
0x10000: Number of bytes to read.
-
4. Perform Boundary Scans
Boundary scans check for connectivity and functionality of the IC pins.
- Use urJTAG or OpenOCD to perform boundary scans.
- Example in urJTAG:
cable jtagkey detect bsdl path/to/bsdl/file.bsd svf boundary_scan.svf
Step 4: Best Practices for JTAG Debugging
- Secure the Connection: Use short, reliable wires to minimize noise.
- Verify Pinout: Double-check the JTAG pin connections to avoid damaging the device.
- Backup Firmware: Always back up the original firmware before making changes.
- Use Correct Software: Ensure the tool you’re using supports the target device.
- Monitor Voltage: Ensure the target device operates at the correct voltage level.
Applications of JTAG
- Debugging firmware and software
- Flashing new firmware or bootloaders
- Extracting data from memory for analysis
- Diagnosing PCB manufacturing defects
- Reverse engineering hardware
Troubleshooting
-
Device Not Detected:
- Verify the wiring and pinout.
- Ensure the target device is powered on.
- Check voltage levels for compatibility.
-
JTAG Errors:
- Ensure the correct configuration file is used.
- Try lowering the JTAG clock speed if communication fails.
-
Permission Issues:
- On Linux, ensure you have proper permissions to access USB devices (use
sudoor configureudevrules).
- On Linux, ensure you have proper permissions to access USB devices (use
Conclusion
JTAG is an invaluable tool for debugging and programming chips at a low level. By understanding the basics of JTAG hardware and software, you can read chip memory, debug firmware, and perform boundary scans. Experiment with different tools and configurations to fully utilize JTAG in your projects!